| Home - Back Issues - The Team - Contact Us |
 |
| Volume 10 |Issue 23 | June 17, 2011 | | |
|
|
Cover Story Virtual Space Real Crime With the developing and expanding computer and cellular technologies, human lives have started to evolve and revolve around the wired and wireless networks. While enjoying the staggering benefits of these technologies, which is digging deeper into our lives with every passing minute, are we ready to defend the threats and risks it brings along? Are we even aware of the dangers that may be unleashed if such cyber technologies are misused? AANTAKI RAISA
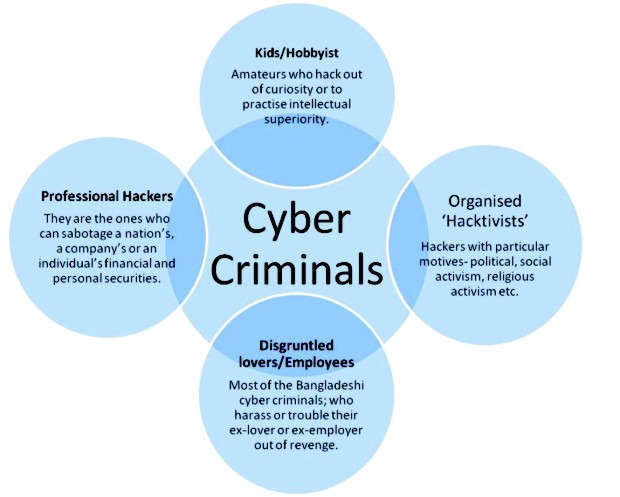
Zarif (not his real name) learned webpage designing and some basic programming from his elder brother when he was in school. Now, a BBA student at a reputed university, Zarif is an expert at web designing and different programming languages. “Programming was fun. But when I started to learn about hacking, making micro virus, I became more and more curious in this area,” he smirks while he mentions. 'Phishing' is like a piece of cake to him and phishing is the cyber crime Nusrat was victimised by. “All you have to do is create a webpage that looks like that of an organisation, take Facebook for example. As the admin of that webpage, whatever information someone provides there, I get direct access to it; of course there are some technical details I have to go through but these details are kind of a secret and way too complicated for someone non-technical,” he explains with 'wisdom'. Hacking, phishing, spreading viruses are sources of entertainment to Zarif, and to people like him. “When you are using a technology, you better have proper knowledge about it. The rules are of those in real life; if you are not careful enough you will be betrayed, you will be victimised,” he blames it on the not-so-expert internet users.
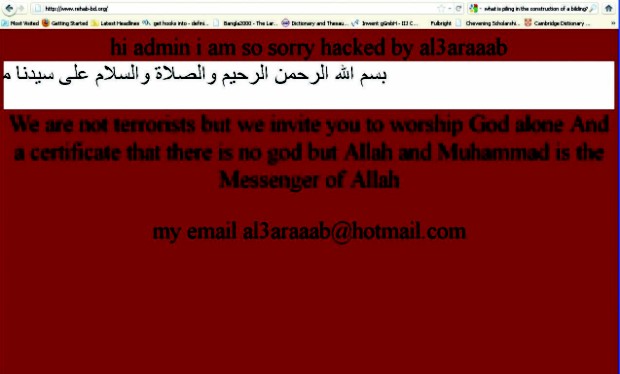
“Though we use the term 'cyber crime' quite frequently, we barely know the definition of it,” says Quazi MH Supan, assistant professor at the Department of Law in the University of Dhaka, “and there isn't any concrete definition of cyber crime, there shouldn't be any because of the ever changing nature of the modern technologies and the crimes related to them.” Though there is no standardised definition, the Information and Communication Technology Act, 2006 of Bangladesh, which, according to Quazi is “a cut-paste of the Indian cyber act”, mentions some specific crimes that fall under the cyber crime category. “Though it includes cyber crimes like internet pornography, harassment, religious and social corruption, major cyber crimes like copyright infringement or privacy violation have not been included as cyber crime,” complains Quazi. He says that, even the text messages sent from the mobile operators to their subscribers or government information texted to mobile subscribers fall under cyber crime, according to the International Cyber Crime Convention (active since July, 2004). He adds that if a mobile operator had sent its subscribers unwanted text messages, they would have been bankrupt to pay the fine in Canada (according to the CAN-SPAM Act). We download free movies, music, books and assorted things from the internet and thus violate the copyright infringement act. Though uploading and downloading pornography is illegal in Bangladesh, it is the most widely practiced cyber crime here. Whereas the Internet Service Providers (ISPs) should have been responsible for monitoring such crimes, we aren't practicing any such policy. Due to the lack of awareness and knowledge, people in Bangladesh are easy prey for cyber criminals. “With the developing technology, cyber crime is improving and increasing as well,” says Quazi. Cyber crime, which probably started with spam mails and Trojan attacks in Bangladesh, has now extended to debit/credit card forgery, cell-phone threats and frauds. “In the last five months, we have received around 90 complaints of cell-phone threats and frauds and we have deactivated around 110 SIMs,” informs Md Masudur Rahman, Assistant Deputy Commissioner (ADC) of Dhaka Metropolitan Police (DMP). These are the numbers of the crime cases filed; the actual number of such crimes committed is much higher and statistically unknown to the authorities. To make things worse, it's not just the number that's increasing in this genre of crime; the intensity and severity of the crime is increasing too.
On September 5, 2008, the Rapid Action Battalion (RAB) authorities discovered their website flashing 'The government does not take any step for ICT development but passed a law about anti-cyber crime…You do not know what the cyber security is or how to protect yourself…Listen, hackers are not criminal. They are 10 times better than your (RAB) experts. We are genius beyond your imagination'. Apparently, the RAB official website was hacked by Shahi Mirza, Md Ishtiaq, Zayedul Hossain and Tawhidul Islam who were traced and then arrested and later sent to jail by the joint investigation of RAB's intelligence and communication wings on the following day. “After hacking the RAB website, the hacker faked his IP address. But he used his name and valid email address during the defacement. By tracking his email address RAB got his address and mobile number and subsequently RAB was able to find out the hackers,” informs a RAB media personnel. RAB's anti-cyber crime team along with RAB 10 also successfully caught the culprits who posted obscene and satirical pictures of some noted politicians of the country on Facebook. But these examples are rather the exceptions in the stack of many unresolved cases. In 2010, the Prime Minister's website was hacked by an Indian hacker, in March of the same year 20 Government district portals were hacked, recently in 2011 a good number of ministry websites were hacked too- none of the criminals have been arrested or even identified yet. The mentioned cases were highlighted in the media, due to the fact that those were affiliated with the government. But it's not just the government websites or the defense websites that have been hacked. The corporate companies and the individuals of this country are also vulnerable to cyber crime in a multitude of levels but their stories are barely heard of. Colonel Zia, director of RAB's intelligence wing says, “Our intelligence wing is currently dealing with a number of cyber crime cases affiliated with corporate companies. But these companies do not want these issues to go public as it might harm their reputation”. “For example, we worked on the Eastern Bank case when they got hacked; but they didn't flash the news because it would create panic among its customers; moreover this sort of news badly harms a company's credibility,” he continues. But Zia thinks these companies should at least let its customers know about any such cyber threat or attack otherwise these customers will have to pay for the company's lapse in cyber security. When cyber crime is committed against an individual in Bangladesh, it's mostly done through social harassment than financial damage. “This is one of the main reasons that cyber crime cases are not filed very often. In these cases, the victim is often scared of more harassment and deterioration of reputation,” says professor S Aminul Islam, Department of Sociology, University of Dhaka. And that's how cyber criminals get away without even having to deal with law and enforcement. A few months ago, The Daily Ittefaq reported that a number of women in Dhaka were abandoned by their fiancés as there were obscene pictures of those women on Facebook. Nothing was done to punish the culprits behind those fake profiles. Sakib received an email a few months ago which contained the detailed list of his phone calls, texts and even the content of the texts. The mailer asked for money to keep his personal information private. Sakib didn't know what to do; he didn't know whether to go to the police or to give money to this person or to complain at his mobile service provider. He remained quiet and fortunately nothing happened.
But one cannot always keep quiet and do nothing. Rafia (not her real name) is one of the brave-hearts who showed the courage to stand against this cyber harassment and demand justice. “But you have to know under what circumstances I had filed that complaint to the police,” says Rafia. “This man, Aleem, who had been harassing me, is an uncle of mine. But as he was my age, I had a friendly relation with him,” she continues, “But when my parents went abroad and I was alone he started behaving differently.” This uncle cum friend of Rafia seems to have misinterpreted the friendship and when he was refused by Rafia, he started harassing and disturbing her. At one point he forcefully took her cell-phone, collected her personal pictures, contacts and other information from it and created a fake profile from her name on Facebook. He added her friends and her brother from that fake profile. He posted some tampered pictures of her and wrote disturbing texts on her wall and status. He kept calling her, her brother and mother, first to malign her and then to ask money in return to delete the fake profile. Rafia requested her mami (aunt) to ask her brother Aleem to stop this, but Aleem didn't. As the harassment and the story of it spread and went over her head, Rafia, with the help and suggestion of her friends and teacher Shajib, filed a GD (General Diary) at the Kotwali police station in Chittaging. “If I gave into his threats, I would have to remain his slave for the rest of my life,” says Rafia. “The police officers at the Kotwali station were really helpful. They listened to my story, took the statements of other witnesses and eventually arrested Aleem,” she adds.
“The legal procedure is to communicate with the Interpol and collect the password of the profile from Facebook. But it wasn't possible for us but within seven days, we arrested Aleem, took him in remand and collected the password of the fake profile from him. He had confessed his crime in remand and after collecting the password from him the police had the necessary evidence,” says Sadip Das, sub inspector at the Kotwali station who was involved with the case. Aleem has not been granted bail but the court hasn't yet pronounced its verdict. But Aleem's family members still threaten Rafia. “I have been thro ugh a time when I felt like dying. The password he used for that fake account was 'callgirl' and this is nothing compared to what he has said about me to his and my friends, families and acquaintances,” she adds. But what she did is exemplary and worth following. Her triumph is the proof that cyber criminals can be caught and punished in this country. But the number of such criminals who are actually caught remains very few in Bangladesh. “Countries that have ratified the International Cyber Crime Convention are supposed to monitor, investigate cyber crimes and capture and punish the cyber criminals,” says Quazi, the assistant professor of law at the University of Dhaka. According to him, though Bangladesh doesn't have a proper monitoring body, the major problem behind the cyber criminals not getting arrested is that we don't have efficient and well-equipped investigation teams in police, RAB or CID. “As the cyber technology is developing, the expertise of the cyber criminals is enhancing as well. If our defense doesn't stay a step ahead, we will not be able to prevent cyber crime,” adds Quazi. According to him, as our intelligence forces are not well trained and well informed of the laws and acts regarding cyber crimes, police often is reluctant to take complaints against such crimes.
Another issue that makes cyber criminals almost next to impossible to detect is the very nature of the crime– it's cyber after all and it takes place in a virtual space. “If you kill someone with arsenic or cyanide, you can get the evidence even after a year from the dead body, but when a crime is committed through computer, the evidence can be deleted before the next morning,” mentions Quazi. He also informs that, many a time, suspects are taken in remand and forced to confess to the police; but such confessions are not granted as evidence at the court. Masudur Rahman, ADC at the DMP also admits the difficulty in collecting evidence against the cyber criminals and tracking them. “Suppose someone is giving you threats over the cell phone. We can get the number but as most SIMs are not registered, it becomes almost impossible to track the criminal,” says Masudur. He also mentions the hurdle to detect a criminal when s/he commits the crime using a computer at a cyber café. “Our cyber cafes do not keep proper record or monitoring of the users. So even if we can trace the MAC and IP address of a criminal, it's not possible to track him/her physically if s/he uses cyber café,” he adds. Due to its novel nature, cyber crime is not always taken as seriously or thought as harmful as it can be both by the potential victims and by the criminals. Zarif, the 'anonymous' hacker, thinks when he hacks someone or infects a computer with virus, he does not cause any mortal danger. But according to professor S Aminul Islam, “Though cyber crime is often considered as a victimless crime, its impact can be deadly.” “As this crime doesn't have any border, its grasp is vast. Cyber crime can jeoperdise national security and break up families,” he adds. But Ahmed, an engineer at a telecommunication vendor says that pornography, if it's not a child porno, is a source of entertainment for many; if the porn is made commercially why would it be harmful or illegal to download and watch it? Countering Ahmed's argument, Islam says that besides the fact that pornography is illegal in Bangladesh, unacceptable in our culture and morally degrading, it has played a role in breaking families apart and causing unrest in the society. “We had studied a case where a husband, who was addicted to internet pornography, had forced his wife to enact the things showed in the porn. As the wife was doing those things against her will, it was a rape. Due to her husband's indulgence, she had to suffer both mentally and physically,” Islam explains.
In 2010, when an Indian hacker hacked the PM's website, he declared a cyber war against Bangladesh. “And we are not prepared or equipped to fight this war,” says Quazi. Both Quazi and Masudur admit that our police and the cyber crime wing do not have proper training to combat cyber crimes. RAB doesn't even have a separate section for cyber crime. “Our intelligence officers voluntarily work on such cases, using and implementing whatever resources and knowledge they have,” mentions Col Zia, the director of the intelligence wing. Access to Information (A2I), a UNDP project that patronises the government websites, has also failed to provide protection. “When we created the websites and portals for the public,” says Naimuzzaman Mukta, the People's Perspective Specialist at the A2I, “we made all information accessible as there weren't anything classified.” “To maintain the simplicity of the sites, we did not put much effort on their security,” he admits. “But websites which contain classified and confidential information, such as the website of the Ministry of Finance, have been well protected since the beginning and haven't been hacked yet,” adds Mukta. The fact is, no matter how securely a website is built or an account is maintained, hackers find their way through. Websites of the CIA and the FBI haven't been able to protect themselves from these evil geniuses. But measures should be taken in individual, corporate and national levels. Quazi mentions some precautions that can be taken to protect one from cyber crimes: Always use firewall to prevent unauthorized network access and insure secured communications. Do not download free software or files from any and every site; most of them have malicious software (malware) attached to them. Do not download any email attachment without scanning it for virus Do not use cyber cafés; most cafes have keylocker software installed in their computers which can record one's email address and password and basically everything that is typed. Decrease the digital divide- financially, socially and age-wise by providing proper technological knowledge and access to all regardless of their backgrounds or status Create and implement proper policies on the national level
Masudur talks more on national level precautions and law amendments as he suggests about the measures that can be taken. According to him, cyber crime is and will be increasing; the legal sections regarding this crime need to be revised and polished, cyber crime must be taken under the cognizable crimes so that people can case FIRs (First Information Report) against such crimes. He also points out the ambiguities in the laws regarding cyber crime, “A cyber criminal can be jailed for a maximum of 10 years and can be fined up to one crore taka. But what if the victim of the crime commits suicide? Will the punishment be the same? Should it?” He continues, “And who gets to keep the money collected from the fund- the victim or the government? And what if the criminal doesn't have one crore taka? There is no mention of alternate punishments in the cyber law.” The human mind is a great and uncontrollable weapon. Without strict implementation of the laws, vigilant monitoring and exemplary punishment, the acceleration and austerity of cyber crime cannot be controlled. In parallel to that, common people need to be educated and made aware of the common threats, precaution measures and law and enforcement services that can help them. The World Wide Web is a web full of limitless possibilities and abysmal dangers where, according to Zarif, “Might is right and the fittest will survive. It's a jungle out there and you better have your weapon- your mind- honed.”
Copyright
(R) thedailystar.net 2011 |
||
 A
A Both people mentioned above are affiliated with cyber crime; the former as a victim and the latter as a criminal. Last year's celebrity pornographic scam, the hacking of official websites of some crucial ministries this year have made cyber crime a buzz word in this country.
Both people mentioned above are affiliated with cyber crime; the former as a victim and the latter as a criminal. Last year's celebrity pornographic scam, the hacking of official websites of some crucial ministries this year have made cyber crime a buzz word in this country.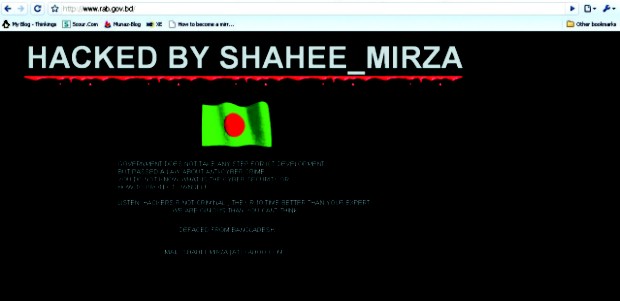
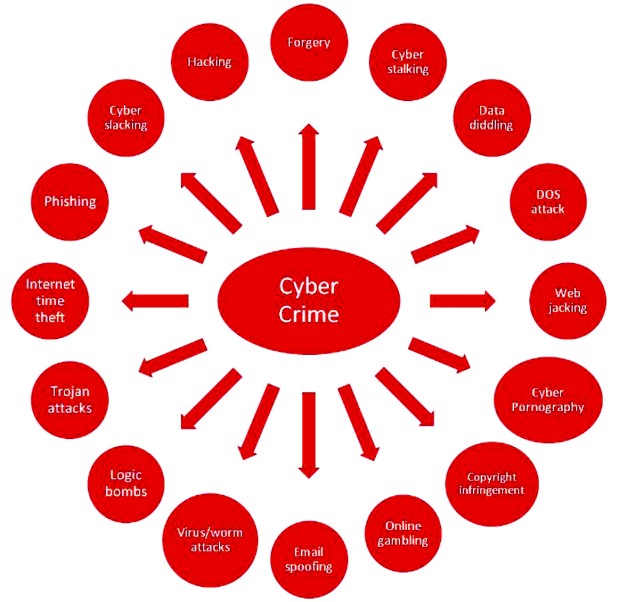
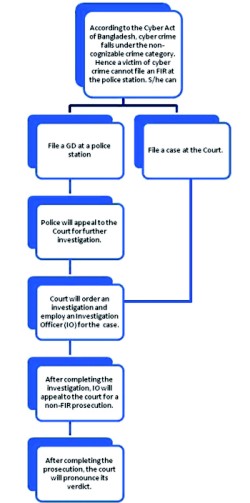 “Moreover, although we have an ICT Act, we do not have proper policies to implement it. According to this act, a cyber tribunal and a cyber appellate tribunal are required to handle the cases regarding this area but none of such tribunals exist! ” adds Quazi. Added to that, mentions Quazi that, the ICT Act is flawed on many levels. It lacks some vital branches of cyber crime and it doesn't have proper provisions to prevent a lot of them. “It doesn't force the ISPs to monitor crimes like downloading or uploading pornography or copyright materials,” he informs.
“Moreover, although we have an ICT Act, we do not have proper policies to implement it. According to this act, a cyber tribunal and a cyber appellate tribunal are required to handle the cases regarding this area but none of such tribunals exist! ” adds Quazi. Added to that, mentions Quazi that, the ICT Act is flawed on many levels. It lacks some vital branches of cyber crime and it doesn't have proper provisions to prevent a lot of them. “It doesn't force the ISPs to monitor crimes like downloading or uploading pornography or copyright materials,” he informs. 
 Upgrade your anti-virus regularly.
Upgrade your anti-virus regularly.