| Home - Back Issues - The Team - Contact Us |
 |
| Volume 11 |Issue 50| December 21, 2012 | |
|
|
Cover Story Privacy Matters Phishing, hacking, cybercrime, eavesdropping, spamming and viral marketing – are buzzwords of today's internet-dependent society in which the benefits of 'tech-savvy-ness' comes with its price – a growing trend of intrusions. Reaffirming computer security basics and stretching our boundaries of online privacy a bit further can effectively minimise the potential risks we remain exposed to in the Information Age. Zahir Hassan Nabil
Off to a graduate school in the UK, Tanvir (not his real name) was just settling down trying to cope with his courses and adjusting to a new lifestyle. At this time he sent his father an e-mail mentioning Lloyds TSB - the name of the bank he had opened an account with. Within the following week, he would receive an e-mail replicating the interface of Lloyds TSB, claiming that it needed to confirm his identity by asking his username, password and other details. Many of us by now know that these accounts of forgery are called Phishing that we all are prone to on the internet. But how did someone else know that Tanvir had subscribed to that particular bank? When he had sent that e-mail to his father, the information was 'eavesdropped' on its way to the mail server. Some hackers put to use computer programmes and devices to constantly monitor internet connections to track people's personal information. These programmes search for particular keywords in the information being transferred. On finding someone from a particular e-mail address writing the name of a particular bank in an e-mail, they would send a Phishing mail to deceive and obtain more information about that person. Needless to say if they are successful, you may end up bankrupt.
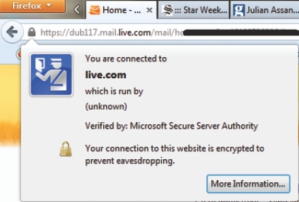
In Bangladesh, phishing is not taken seriously because only a handful of people use internet banking and most internet activities do not involve monetary transaction. A researcher in computer security, Dr Ragib Hasan, assistant professor and UAB SECRETLab director at University of Alabama, says, “As Bangladesh moves into the age of e-commerce, we face a greater danger. When financial motivation is present, real criminals are going to get into cybercrime and defraud banks and the public.” “Information can be eavesdropped in similar ways from chatting software like msn and yahoo messengers, skype and social networks, if the internet connection is not appropriately secured,” says Shohrab Hossain, a faculty member of Bangladesh University of Engineering Technology (BUET), Computer Science and Engineering (CSE), a doctoral candidate at University of Oklahoma. As a remedial alternative, enforcing secured or encrypts connection (https) on the browser and elsewhere may prevent hackers from scanning or reading the information being transferred, which in turn should minimise eavesdropping risks. “When https is enacted, although it is possible to intercept data in its transit, it is not generally possible to extract useful information from the encrypted messages,” says BUET CSE faculty member Yusuf Sarwar Uddin, a doctoral candidate at University of Illinois. Dr Ragib Hasan, however, explains that https only ensures end-to-end security, “If two people, Alice and Bob, are communicating over an https connection, then no one sitting in between them can eavesdrop on their communication. But someone can still eavesdrop at one of the ends, by installing a spyware in Alice or Bob's computers. Such spyware can record the conversation or snoop on email before that goes into the secure channel. Then the recorded audio or collected emails can be transmitted to the hacker by the spyware.” “When a spyware is installed in a computer, it can capture all input and output data. For example, the spyware can run a keylogger which will record every keystroke, which means the spyware can steal passwords for any website or any software the user has logged into. Spyware can also take screenshots, steal data, and send them back to the hackers through a covert channel,” he adds. There are, of course, more ways of intrusion. One fine morning, Sonia Khan, a journalist, discovered all her e-mail addresses were deleted from the address book and her inboxed e-mails had vanished. “I am not sure whether I downloaded an e-mail attachment from an unknown person,” she wonders. Her case was the most common instance of security breach that may have happened through downloading malicious e-mail attachments. “Usually, the e-mails and attachments are disguised as something benign and attractive (e.g., an e-card, or it claims that a friend's account has been compromised by the attacker). Alternatively, the victim may be duped into clicking a malicious link on facebook or the likes. As soon as the user clicks on such a link or attachment, the spyware gets installed and takes over the victim's computer,” explains Dr Hasan. Also, some malicious programmes automatically gather random e-mail addresses put in public from the internet. It uses modules like a password generator that keeps trying words from dictionaries, commonly used sequences of numbers etc. to take over mail accounts. Once it infiltrates an account, it enlists all e-mails stored in its address book and further spams them with advertisements or sends a phishing trap. It may be that Sonia had filled out a form inadvertently on the internet with her e-mail that was sold to marketing companies for viral marketing, a technique to promote products, bombard e-mails with malwares or petitions asking to deposit money, declaring (fake) prize winners and eventually asking for money etc. Dr ABM Alim Al Islam, a BUET CSE faculty member, said that apart from installing an antivirus, there are a few steps everyone should take to avert eavesdropping and all sorts of malware. Those are, “Using and upgrading prominent browsers like Firefox, regularly installing operating system (e.g. Windows) security updates, avoiding downloading e-mail attachments from unknown senders and visiting websites linked in such e-mails, and using encrypted data exchange (might be through https),” he recommends. The experts unanimously agreed that besides ensuring computer security basic and safely using the internet, every vigilant netizen (portmanteau of internet and citizen) must limit exposure of private content on the internet, which is a trail that leads to the compromise of security.
Beyond online privacy Suppose it is your friend's birthday and you wish him writing 'Happy Birthday, have a blast”, facebook will generate advertises of greetings cards, cakes, flower bouquets on the advertisement panel for you to choose a means of sending a gift. In Bangladesh, it is not an effective way yet to advertise because we are not very reliant on e-commerce. But in developed countries it is, for buying gifts online. Similarly, the moment you set your location to “Dhaka, Bangladesh” you start receiving ads from local advertisers. The moment you tag your photo with a friend at a local restaurant, the easier it becomes for facebook to get an idea about your tastes and accordingly advertise more relevant products for you and your friends. You spend hours and hours (mostly talking casually) on the social network, the network in turn uses you as an unpaid employee and sells your 'socialising' as marketing data to the advertisers while the advertising revenue finds its way to its owner's velvet pocket. But why do we constantly surrender our privacy despite reminders of the perils and drawbacks? Anis Pervez, a sociologist and information science specialist, offers an apt explanation, “On facebook, one observes how s/he is being responded to or appreciated through the many likes on a given status. Besides, the postings are relatively permanent, unlike the real world; one can come back to narcissistically observe how s/he was appraised. This is one reason why many people expose their own privacy on the internet despite knowing its potential risks.” He elaborates further, “Technologically speaking, it is also because we Bangladeshis, have become overwhelmed often suddenly being given the chance to use the social networks, from almost a primitive telecommunication technology prior to that. Globally, people are more aware of their privacy.” Of course, facebook does not give out information to spammers but if someone's private information is not appropriately protected on the internet, in comparison to facebook's marketing and advertising strategy, one can imagine to what extent unprotected information remains exposed to in the web. Legal Measures against Cybercrime Even so, what are the legal measures against such deliberate instances of infiltration like counterfeiting private content, eavesdropping and hacking over the internet? Barrister ABM Hamidul Mishbah, an advocate at the Supreme Court of Bangladesh, informed that currently there is no 'Cyber Law' in Bangladesh. The only piece of law concerning activities in cyberspace is the Information and Communication Technology (ICT) Act 2006. “It has provisions for offences committed to any computer system. For instance, unauthorised entry into a computer system, distorting or tampering data and hacking into system is a crime or offence under this act. Also, unauthorised entry of someone else from outside the country into a computer system in Bangladesh is considered an offence and is punishable under this act,” he explains. He further adds that apart from the ICT Act 2006, Bangladeshi Law has the Penal Code provisions which apply to offences committed on the internet, including derogatory content published by individuals on blogs, social networking sites, i.e. Facebook, twitter that are offensive or deterring national and international security. The lawyer commented that ICT Act 2006 has been enacted but is not being enforced properly. “The act mandates for establishing a Cyber Tribunal which has not been established so far. The Tribunal is supposed to deal with cybercrime and offences which is not in place, as a result, rendering the ICT Act ineffective and abandoned as of now,” he adds. Formation of law and its enactment are of secondary importance but protecting one's own privacy and ensuring computer security basics come first while using internet-based communication, social networking sites and e-commerce incorporated media. One thing yet to spur awareness among most people is the way they surrender their privacy while using the internet. While maintaining security measures on one's computer and the internet, unnecessary details of one's whereabouts and personal information should be withdrawn from the internet as it makes one susceptible to eavesdropping and hacking. One thing must be realised that social networking and other similar communication technologies (e.g. skype) are 'free' at the expense of our privacy while the choice over the level of exposure therein still belongs to us. In the words of different communication scholars, the internet is just a social space and a society, which we need to understand the same way we understand the real world comprising real people. In a real society, we don't expose ourselves and put our privacy forth for public display but on the internet we do it most often. It is rather recommended to maintain one's presence 'reasonably' on the internet, the definition of which varies from person to person and is left for an individual to decide and set his/her own boundaries. TIPS FROM THE EXPERTS
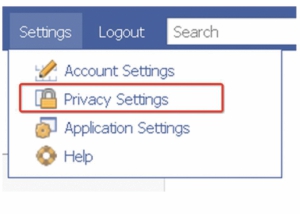
* Online banking uses https by default. Searching on 'how to use https' on google should reveal how to enforce it on different e-mail accounts, facebook and other social networking sites. JARGON BUSTER
* Eavesdropping: Sniffing communication between computers over the internet continuously for confidential information.
|
||||||||||||||||||||||||||||||
Copyright
(R) thedailystar.net 2012 |